
Scientists have devised a series of novel and inexpensive attacks that can severely disrupt mission-critical global positioning systems relied on by the military and a variety of industrial players, including airlines, mining companies, and operators of hydroelectric plants and other critical infrastructure.
Unlike previous GPS attacks, the one developed by a team of scientists from Carnegie Mellon University and a private navigation company exploits software bugs in the underlying receivers. That allows the attacks to be stealthier and more persistent than earlier exploits, which primarily relied on signal jamming and spoofing. Prototype hardware that cost only $2,500 to build is able to cause a wide variety of GPS devices within a 30 mile radius to malfunction. Because many of those devices are nodes on special networks that make GPS signals more precise, the attacks have the effect of disrupting larger systems used in aviation, military, and critical infrastructure.
The PCSS, or phase-coherent signal synthesizer, that they developed simultaneously receives and transmits civil GPS signals. It carries out many of the same things done by spoofers used in earlier GPS attacks. But instead of merely providing false information designed to compromise the accuracy of the GPS readings, it includes data that exploits weaknesses in the firmware of nearby receivers, many of which use the Internet to share their readings with other machines. The success of the PCSS is the result of an almost complete lack of authentication in the devices that send and receive GPS signals.
"Our findings suggest despite the fact that GPS is an unauthenticated broadcast protocol, current receivers treat any incoming signal as guaranteed correct," the scientists wrote in a research paper. "Worse, receivers often run full OSes with network services. Together, the possibility of RF [radio frequency] and ethernet attacks creates a large attack surface."
Journey to the Center of the Earth
One attack described in the paper is able to completely disable a Trimble NetRS. The $19,000 device is the single most popular receiver used for so-called differential GPS networks. Such networks are used for fine-tuning and correcting signals, and include the Continuously Operating Reference Station (CORS) and Networked Transport of RTCM via Internet Protocol (NTRIP) systems.
The "middle-of-the-earth" attack works by instructing the PCSS to set a satellite's semi major axis to zero. That causes NetRS receivers as far away as 30 miles to use the number as a divisor when calculating the satellite's orbit. As a result, the device goes into an endless reboot loop that persists even after the incorrect data is no longer supplied. The researchers created the following video demonstration of the attack:
In all, the scientists devised attacks that worked on the NetRS and eight other GPS receiver models, including those used by consumers, aviation pilots, and operators of industrial equipment. One such attack had devastating consequences for the Arbiter 1094B Substation Clock used as an accurate time source for equipment in electrical power stations. It used the PCSS to set the time one week beyond the current week but otherwise include all other data sent in a navigation message.
The scientists used the technique to simulate rollover events by alternating between high, low, and medium week numbers, eventually shifting its time by around 100 years. Since the Arbiter showed no ability to compare the settings to internal clock settings, it suffered permanent damage when it was exposed to the exploit.
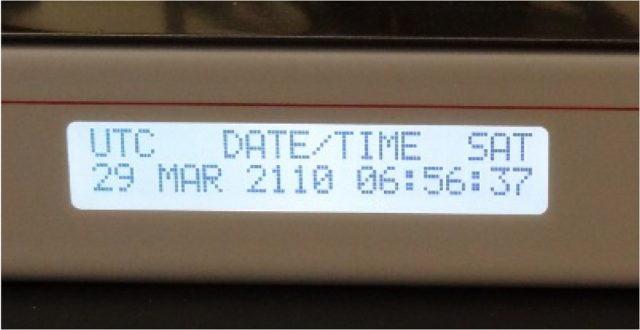
"Multiple days without power, attempts to change the date through commands over the serial console, and reloading the firmware of the device proved unsuccessful for decrementing the year on the clock, rendering the device practically useless as a sub-microsecond accurate time source," the researchers wrote.
EGADS, no easy fix
Because the attacks exploit bugs in potentially millions of stand-alone devices, it's not possible to roll out a single patch for the GPS vulnerability. The research paper proposes what's called EGADS. Short for Electronic GPS Attack Detection System, it would work as the GPS equivalent to the intrusion detection systems used to detect attacks in enterprise networks. EGADS would use rule-based and anomaly-based components to detect bad values and data that deviates from known almanac data.
Longer term fixes will require engineers to build data-level and OS-level defenses into the GPS receivers they design. In theory, military systems already have a solution in place for these attacks. But in many cases, military systems rely on civilian GPS signals, so they aren't immune, Tyler Nighswander, one of the researchers, told Ars.
Besides Nighswander and David Brumley of Carnegie Mellon, the other researchers who wrote the paper included Brent Ledvina, Jonathan Diamond, and Robert Brumley of Coherent Navigation, which provides GPS services and products. They presented their research at the 19th ACM Conference on Computer and Communications Security in October, but the paper only came to wider attention recently.
Now that GPS has morphed from a limited-purpose positioning system into a ubiquitous trusted source for navigation, position and timing, the failure to fix the vulnerabilities carries serious consequences, they warned.
"The intricate nature of today's GPS devices has created a large attack surface," they wrote. "Previous approaches have treated GPS security as an issue of hardware and signal analysis, but many traditional software security lessons have yet to be learned by GPS manufacturers. Until GPS is secured, life and safety-critical applications that depend upon it are likely vulnerable to attack."
Listing image by Coherent Navigation
reader comments
69